FortiMail - Systems Settings and Administrative Options
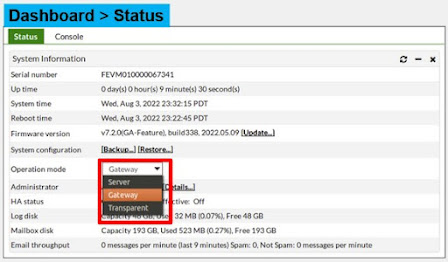
Select the Operation Mode The default operation mode is gateway mode – the other modes are server and transparent mode. Changing the operation mode requires a reboot as the operation mode changes how the entire appliance works. The operation mode that you are planning to run your FortiMail appliance in should be decided ahead of the initial deployment, as the operation mode is chosen during the initial setup. This can be changed from the Dashboard later on, but will require a reconfiguration of the appliance for it to work afterwards. In email operation having correct time is imperative for correct operation. Timestamps are used for logging but are also placed in mail headers for messages sent on to other MTA’s. As a best practice you should configure your FortiMail appliance to use an NTP server. Domain Name By default the system hostname is the device’s serial number. This name shows up in mail headers so should be changed. The Host name + the Local domain name = the ful